by Nadia Prupis, staff writer for Common Dreams
‘This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem’
The president of Microsoft slammed the National Security Agency (NSA) for its role in the ongoing global malware attack, saying it was “yet another example of why the stockpiling of vulnerabilities by governments is such a problem.”
“Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage,” Brad Smith, president and chief legal officer at Microsoft, wrote in a blog post on Sunday. “An equivalent scenario with conventional weapons would be the U.S. military having some of its Tomahawk missiles stolen.”
“The governments of the world should treat this attack as a wake-up call,” Smith wrote.
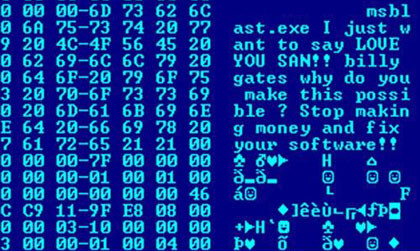
Last Friday, stolen NSA malware was used to attack hospitals, universities, and businesses around the world, ultimately hitting hundreds of thousands of computers in more than 150 countries, including the U.S., reaching what Europol—Europe’s leading police agency—described as an “unprecedented level.” It forced the closure of multiple hospitals and ambulance companies, among other services and institutions. As of the weekend, it had spread to China, and security experts say it could just be getting started.
Smith’s blog post appeared to be official confirmation that the NSA developed the virus.
“[T]his attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem. This is an emerging pattern in 2017,” Smith wrote.
The tool, known as “WannaCry,” was stolen by a group known as the Shadow Brokers, using a weaponized Microsoft vulnerability developed by the NSA against the warnings of cyber security experts. WannaCry operates by locking the user out of their system, encrypting the data, and demanding a ransom via Bitcoin to release it, starting as high as $300.
Microsoft in March released a patch for users to remove the vulnerability, but long-standing delays in updating major systems—such as the National Health Service (NHS) in the U.K.—exacerbated by a lack of support from the software company, allowed the attack to spread quickly around the world.
“The fact that so many computers remained vulnerable two months after the release of a patch illustrates this aspect,” Smith wrote Sunday. “As cybercriminals become more sophisticated, there is simply no way for customers to protect themselves against threats unless they update their systems. Otherwise they’re literally fighting the problems of the present with tools from the past.”
Still, he said, the greatest burden should fall on the government. He reiterated Microsoft’s call for a “Digital Geneva Convention” to create new requirements for governments to report vulnerabilities to vendors rather than stockpile, sell, or weaponize them.
“They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world,” he wrote. “We need governments to consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits.”